FCTF2023
本文最后更新于:2023年8月25日 下午
FCTF2023
[TOC]
web
连连看
这个题关了js再打开,计时就会暂停下来(火狐不可以。。)
ez_session
phpinfo.php
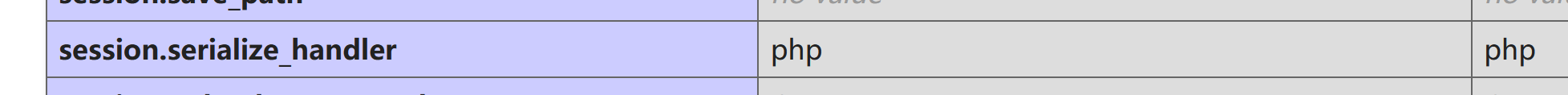
index.php
1 | |
session.php
1 | |
session反序列化
(注意这里的C参数不要加单引号。。)
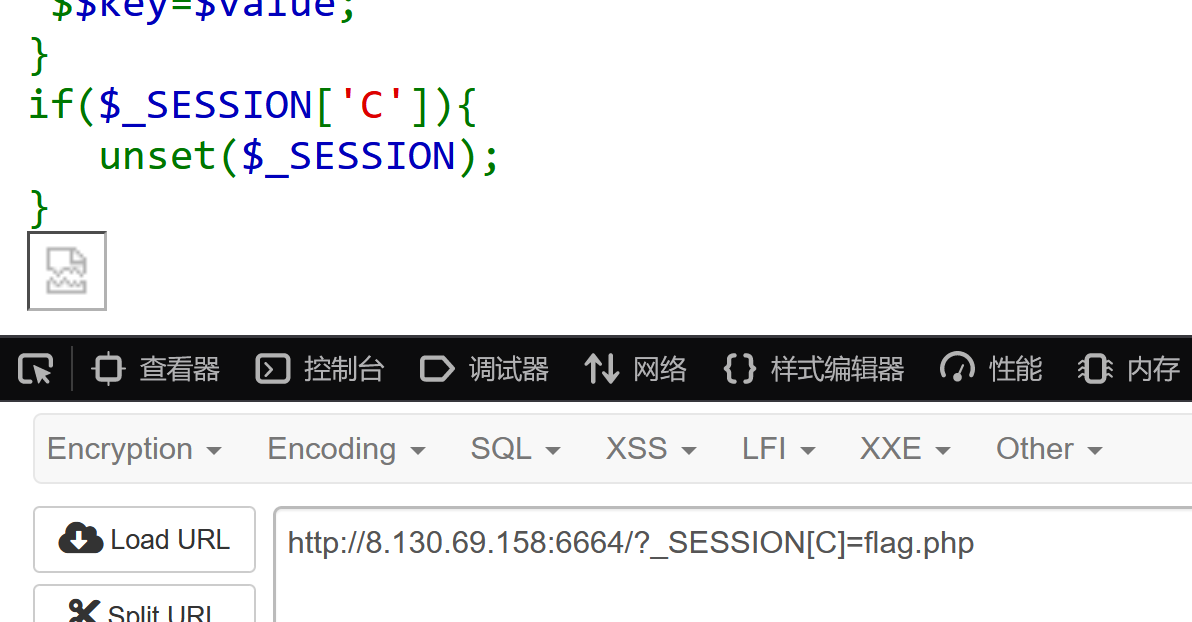
传参:
1 | |
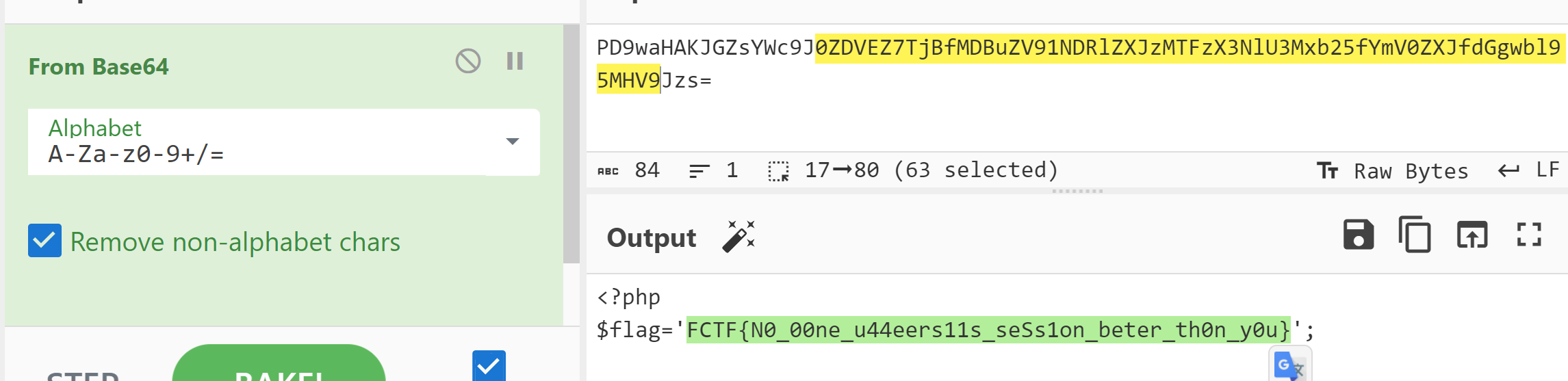
然后session文件变成这样:
1 | |
接着session.php使用php处理器进行反序列化,就会将$flag赋值为flag.php
baby_flask
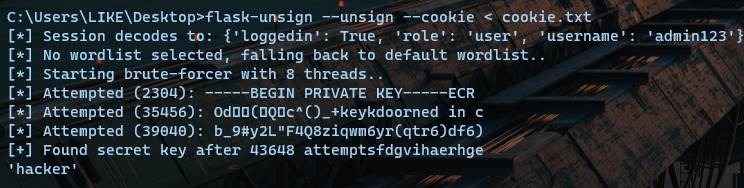
flask-unsign爆破key
flask
secret_key如果是弱口令的话,是可以使用flask-unsign进行爆破的
pickle反序列化
构造poc:
1 | |
ez_login
看网上文章说可以删掉验证码
删掉后确实可以用
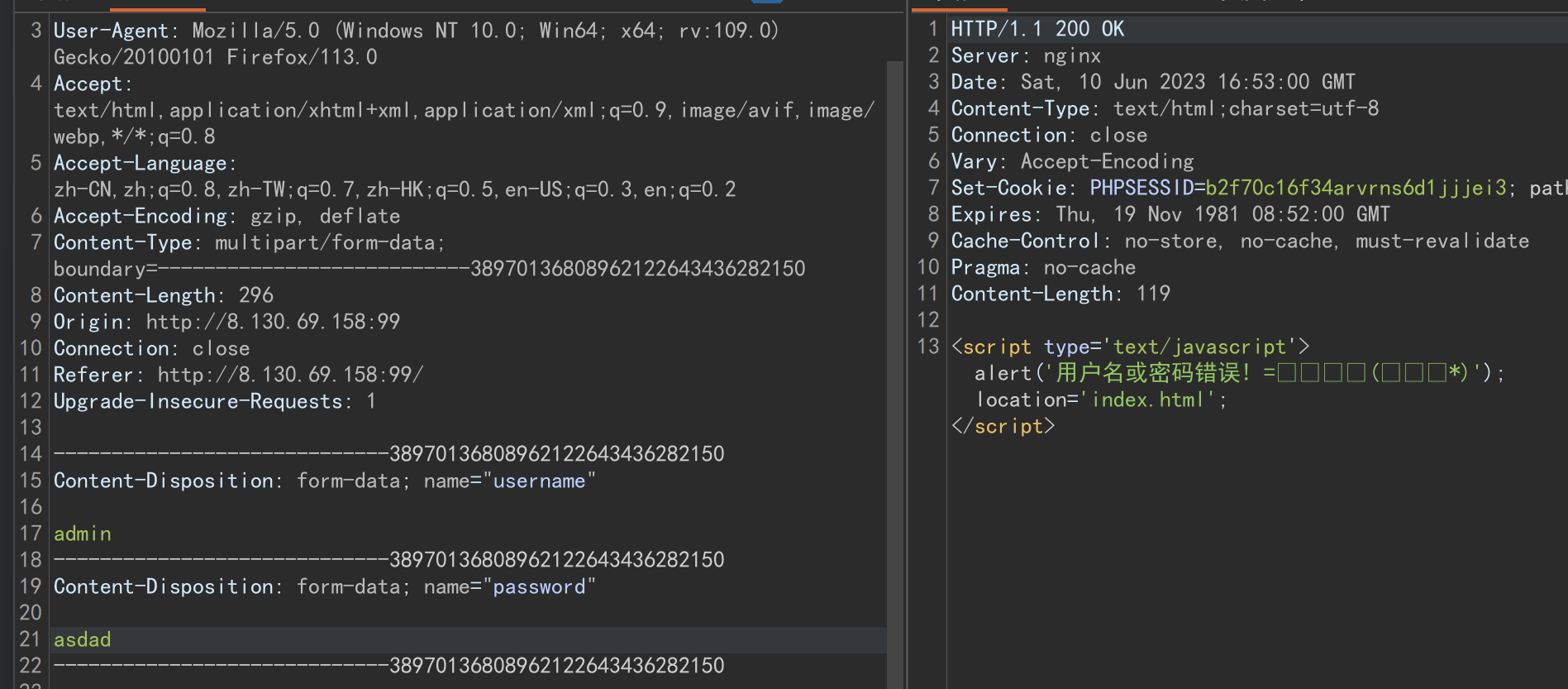
根据这个我们进行爆破,得到密码:password
登录后获得源码:
1 | |
注意filter函数,将 < > 替换为空,所以这里存在反序列化字符逃逸
构造:
(注意要让参数的个数一致)
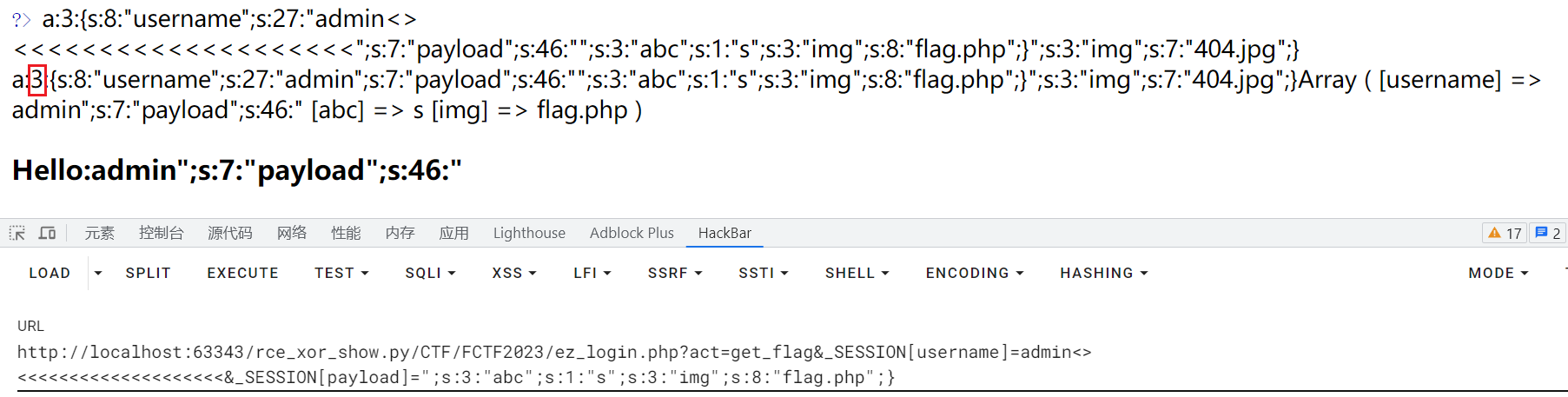
1 | |
misc
这是真签到
FCTF{Welcome_To_FCTF2023_Have_A_Good_Time!}
拼图
使用gaps拼图

猜字游戏
(提示:纯游戏,玩过即有flag)
sgin_hash
使用python脚本爆破,或者使用hashcat爆破
爆学号
1 | |
爆电话
1 | |
古典密码
栅栏+凯撒
baby_Stegan
将docx文件改为zip
然后获得 水印.jpg
使用 BlindWatermark.jar 分离出盲水印

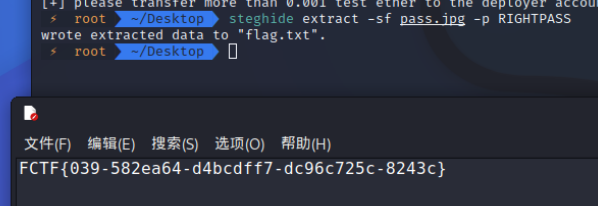
然后使用steghide解密:
baby_hacker
pcapng文件手工分离(使用16进制):
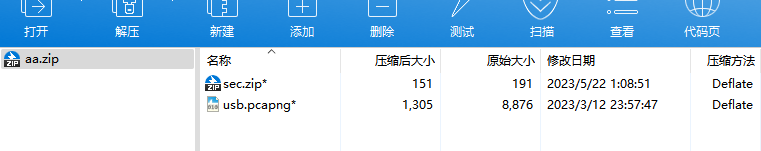
在pcapng文件中分离出一张图片:
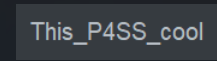
使用该密码解压压缩包:
usb.pcapng中是一段键盘流量
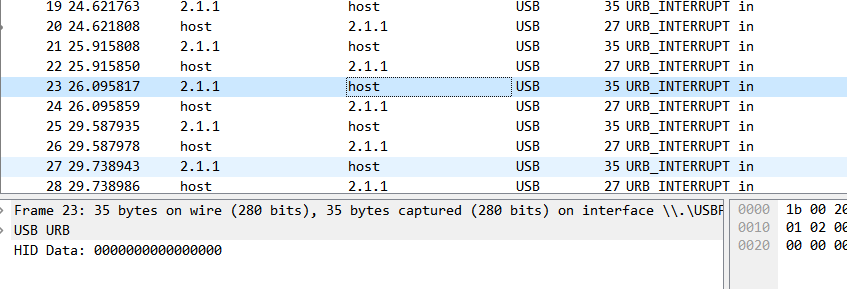
使用tshark提取数据
1 | |
然后使用脚本加上冒号
1 | |
使用脚本将这些数据转为键盘按键:
1 | |
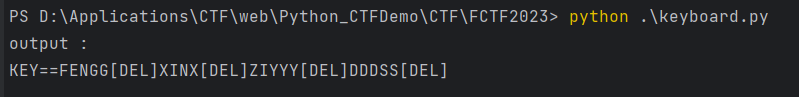
转为小写后解密压缩包得flag([DEL]键是删除键)
blockchain_check_in
very easy blockchain,go fast to check in!
based on Sepolia
第一次写这种区块链的题
首先创建一个metamask钱包
然后去这个网站添加 Sepolia 网络 (这网络真烂,一直进不去)
然后找网站在线挖矿 , 获得 ETH
解题步骤:
首先创建一个账户:
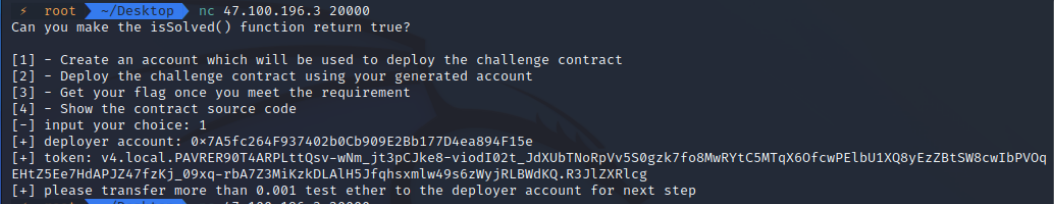
然后我们向这个账户地址转ETH,转完之后使用account部署contract
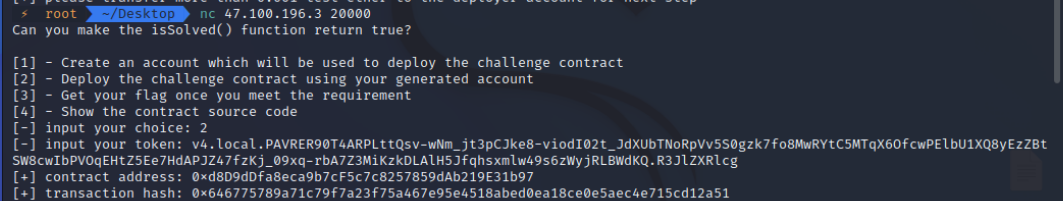
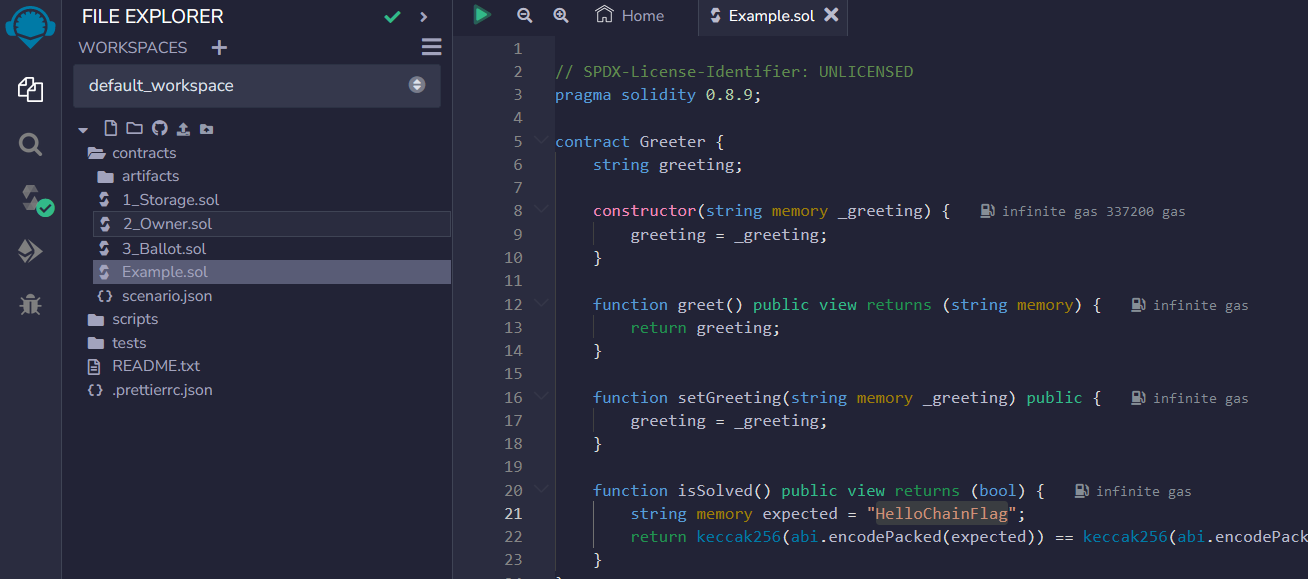
使用在线remix编写,将合约复制到 Example.sol文件中
编译一下:
接着:
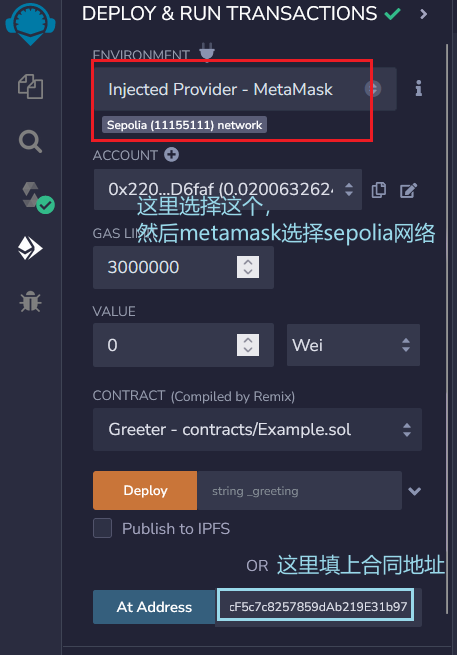
然后调用setGreeting,参数输出字符串 HelloChainFlag
然后metamask就会弹出交易:
再点击 isSolved
这时就得到flag了
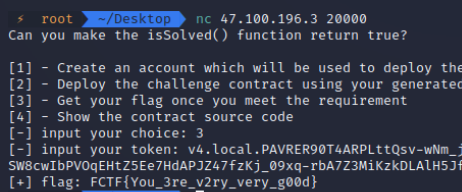
参考文章:https://www.ctfiot.com/53620.html (一摸一样好吧)
osint
保护喵喵
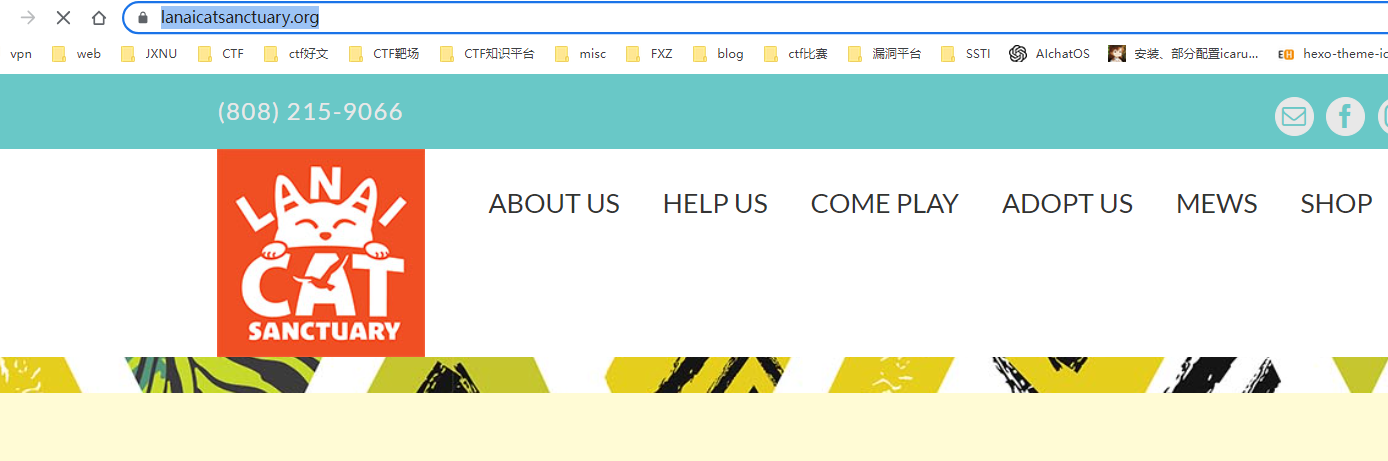
故地重游
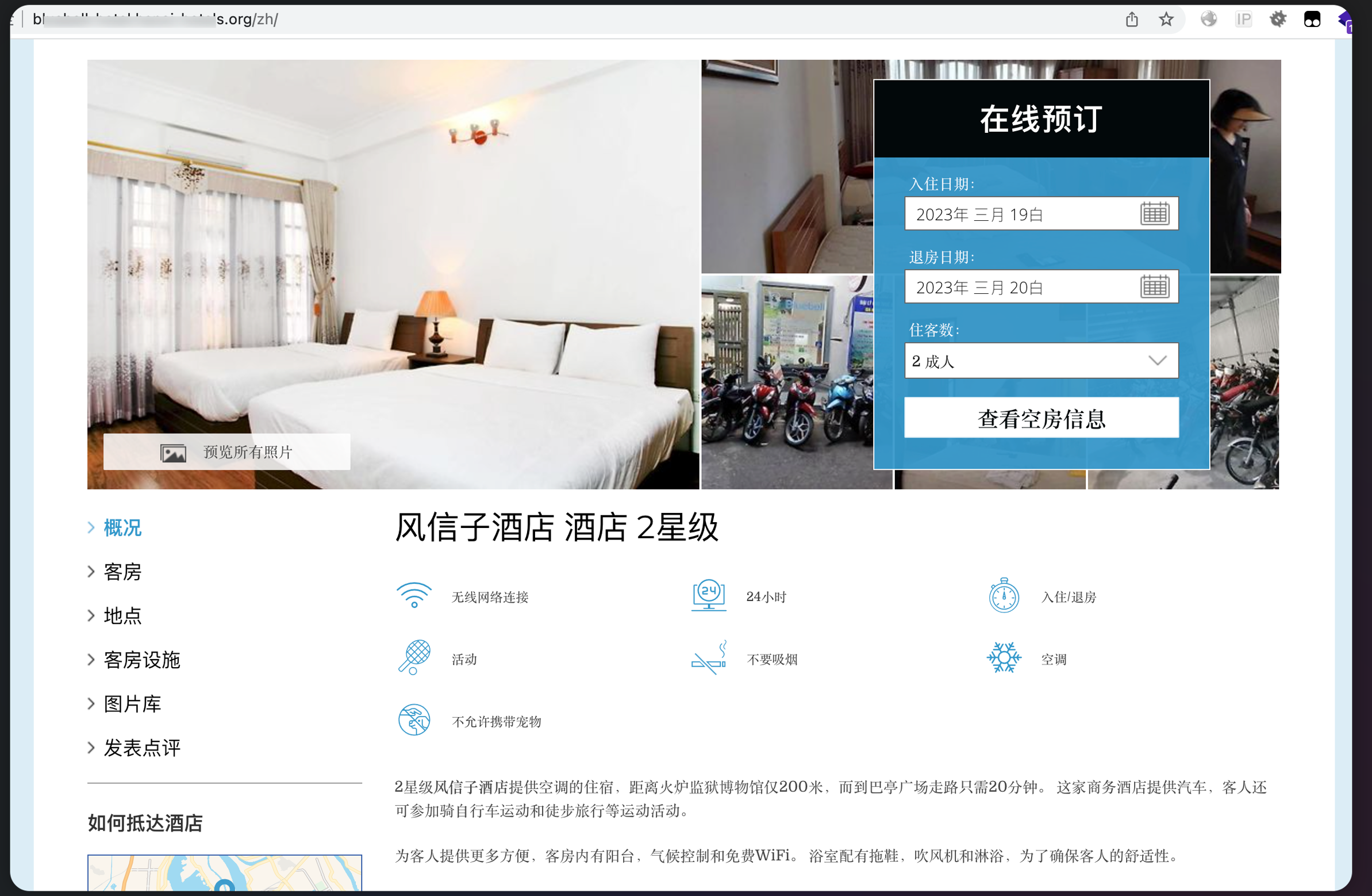
搜索车牌确定为临沂
然后搜原拿铁,在百度地图上找到
去旅游了
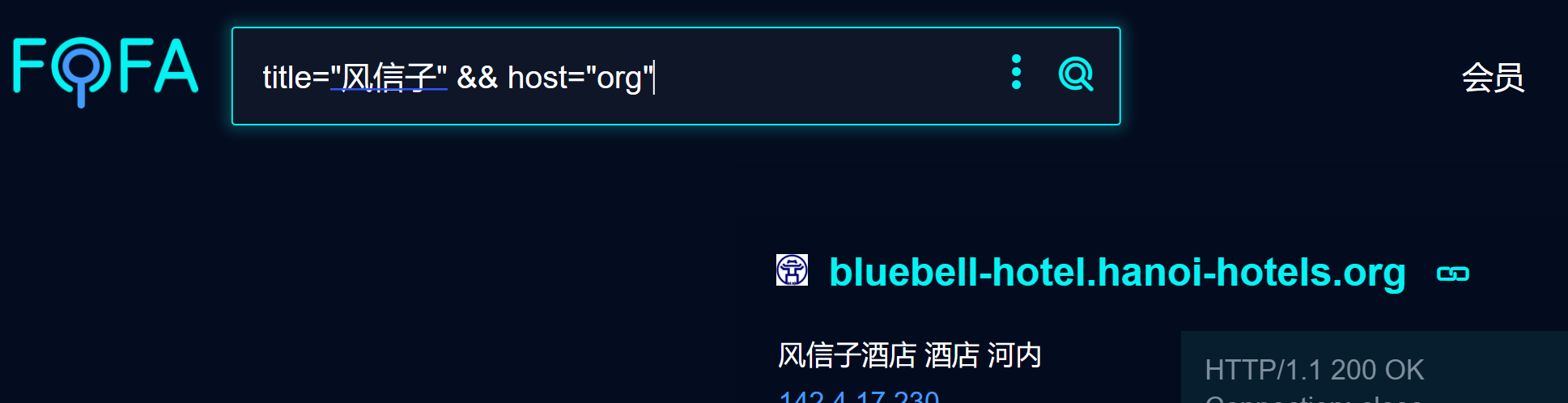
使用fofa
1 | |
re
Click
暴力点100下,或者用ida
pwn
sgin
1 | |
前21个是 FCTF{wow_Pwn_is_v3ry_
0x7d4e7566转为字符为:}Nuf
所以flag:FCTF{wow_Pwn_is_v3ry_fuN}